How to store aes encryption key images are ready in this website. How to store aes encryption key are a topic that is being searched for and liked by netizens today. You can Find and Download the How to store aes encryption key files here. Download all royalty-free vectors.
If you’re looking for how to store aes encryption key pictures information related to the how to store aes encryption key keyword, you have pay a visit to the ideal site. Our site frequently provides you with suggestions for downloading the highest quality video and picture content, please kindly surf and locate more enlightening video articles and images that match your interests.
If you use a password hash as an encryption key you should not store the hash for login purposes. The problem is the code examples Ive seen for shamirs secret sharing is always using integer type secrets and I have bytes type key and I cant split the key into shares. The card let you use them but they can never be extracted from the card. Use the Powershell below to get your environment prepared. 05082018 The key rotation period should depend on your needs.
How To Store Aes Encryption Key. The four types of AES operations as follows note. 1 a secure location to store your key 2 a secure location to store your encrypted password 3 the password for the User account that you need to use in your script. 16042013 Your data that needs encrypting can then be encrypted with the AES key and the AES key encrypted with the pub key from your stored key pair. 01052011 I then take that 256bit AES encrypted string and run it through RSA encryption with my public key which sits server side.
 Aes Encryption With 256 Bit Of Key Length In Mix Columns Each Column Download Scientific Diagram From researchgate.net
Aes Encryption With 256 Bit Of Key Length In Mix Columns Each Column Download Scientific Diagram From researchgate.net
Use the Powershell below to get your environment prepared. StringEncrypter aesEncrypt new StringEncrypter aesKey aesKeygetAlgorithm. 09052011 AES symmetric algorithm where encryption and decryption key is the same is used for instance within Group Policy passwords set by group policy preferences to encrypt those passwords in the xml file being part of the group policy definition stored in SYSVOL. The purpose here is to convert the plaintext data into ciphertext through the use of a secret key. 23042020 What the 4 AES Encryption Operations Are and How They Work. When you need to decrypt you decrypt your AES key then decrypt your data.
23042020 What the 4 AES Encryption Operations Are and How They Work.
Well get into the order of the operations in the next section. Here is the code part of secret sharing. Most smartcards can store a small amount of private keys. The file could be a flat file or an encrypted container thats protected by a password which your application knows up to you to decide but an encrypted container is better. Theres really no safe way to store keys and have them accessible to a web app. 09052011 AES symmetric algorithm where encryption and decryption key is the same is used for instance within Group Policy passwords set by group policy preferences to encrypt those passwords in the xml file being part of the group policy definition stored in SYSVOL.
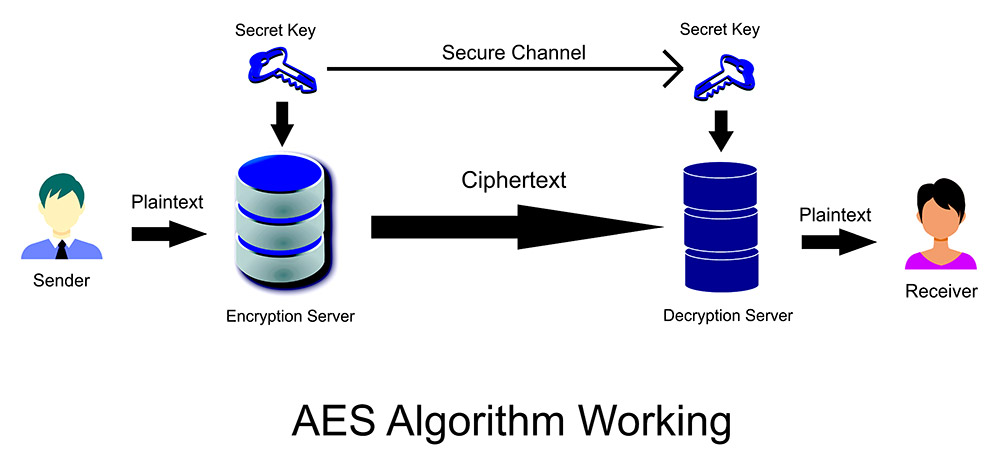 Source: trentonsystems.com
Source: trentonsystems.com
9 horas atrs Im trying to encrypt a file using aes encryption and split the key with shamirs secret sharing. Not secure in the least. To communicate a symmetric key and IV to a remote party you would usually encrypt the symmetric key and IV using asymmetric encryption. As mentioned earlier once we have our data arrangement there are certain linked operations that will perform the scramble on each state. Store the encryption key.
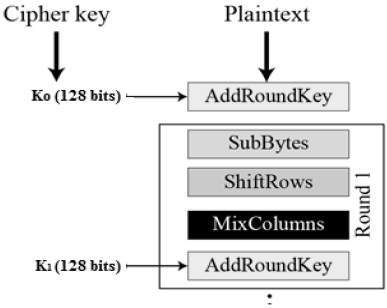 Source: crnkovic.me
Source: crnkovic.me
To communicate a symmetric key and IV to a remote party you would usually encrypt the symmetric key and IV using asymmetric encryption. If you use a password hash as an encryption key you should not store the hash for login purposes. Use the Powershell below to get your environment prepared. String aesEncrypted aesEncryptencrypt StringContent. The purpose here is to convert the plaintext data into ciphertext through the use of a secret key.
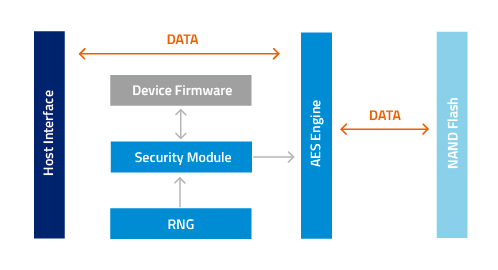 Source: atpinc.com
Source: atpinc.com
Quite secure in my opinion. 01052011 I then take that 256bit AES encrypted string and run it through RSA encryption with my public key which sits server side. 1 a secure location to store your key 2 a secure location to store your encrypted password 3 the password for the User account that you need to use in your script. SecretKey aesKey KeyGeneratorgetInstance AESgenerateKey. In order to decrypt I have to upload a temporary file with my private key and retrieve the necessary data.
 Source: devglan.com
Source: devglan.com
Or even much better let the crypto hardware on the card generate the required private keys for you. What this means in practice is that a password or passphrase becomes part of the key and so data encrypted with AES can only be decrypted with the correct password or passphrase. When you need to decrypt you decrypt your AES key then decrypt your data. In order to decrypt I have to upload a temporary file with my private key and retrieve the necessary data. Obviously Im not going to use that one since the key will be stored in plaintext.
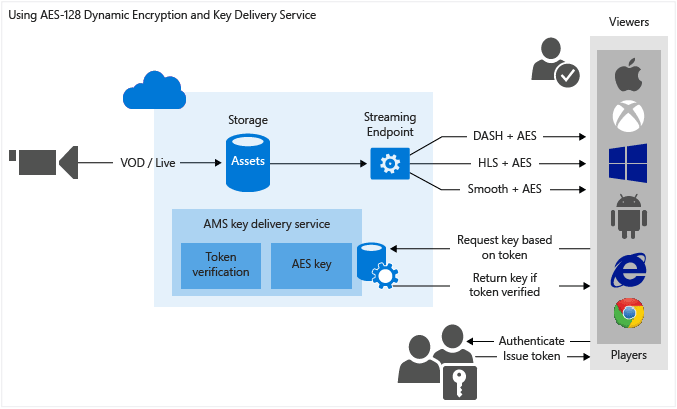 Source: docs.microsoft.com
Source: docs.microsoft.com
Well these are my opinions. Way is to use the Azure Key VaultIts a FIPS-140 Level 2 certified HSM and can perform crypto operations without your application needing access to the keys. The card let you use them but they can never be extracted from the card. 01052011 I then take that 256bit AES encrypted string and run it through RSA encryption with my public key which sits server side. Alternatively if you have a small amount of data you could skip the AES encryption entirely and use RSA encryption.
 Source: transcend-info.com
Source: transcend-info.com
Theres really no safe way to store keys and have them accessible to a web app. 01052011 I then take that 256bit AES encrypted string and run it through RSA encryption with my public key which sits server side. SecretKey aesKey KeyGeneratorgetInstance AESgenerateKey. StringEncrypter aesEncrypt new StringEncrypter aesKey aesKeygetAlgorithm. Learn how to create a secret key for encryption and decryption using Android KeyStoreSubscribe to my weekly newsletter.
 Source: transcend-info.com
Source: transcend-info.com
04022019 Because its a symmetric encryption algorithm in AES there is is just the one key which is a shared secret between the sender and recipient so no privatepublic key pairs. 09052011 AES symmetric algorithm where encryption and decryption key is the same is used for instance within Group Policy passwords set by group policy preferences to encrypt those passwords in the xml file being part of the group policy definition stored in SYSVOL. The problem is the code examples Ive seen for shamirs secret sharing is always using integer type secrets and I have bytes type key and I cant split the key into shares. 10082016 Easy way to storerestore encryption key for decrypting string in java. When you need to decrypt you decrypt your AES key then decrypt your data.

If I print out aesKey I get. 04022019 Because its a symmetric encryption algorithm in AES there is is just the one key which is a shared secret between the sender and recipient so no privatepublic key pairs. As mentioned earlier once we have our data arrangement there are certain linked operations that will perform the scramble on each state. 20082013 Store the key on disk and at the OS level configure file access so that only the account your application is running under can read the file the key is contained in. Way is to use the Azure Key VaultIts a FIPS-140 Level 2 certified HSM and can perform crypto operations without your application needing access to the keys.
 Source: cloudwards.net
Source: cloudwards.net
Well these are my opinions. StringEncrypter aesEncrypt new StringEncrypter aesKey aesKeygetAlgorithm. 23042020 What the 4 AES Encryption Operations Are and How They Work. In case of a decent cipher like AES encryption large number of files with the same key is not a problem so using a single key doesnt result in weaker encryption than using multiple keys. Well these are my opinions.
 Source: researchgate.net
Source: researchgate.net
Learn how to create a secret key for encryption and decryption using Android KeyStoreSubscribe to my weekly newsletter. The four types of AES operations as follows note. Theres really no safe way to store keys and have them accessible to a web app. 05082018 The key rotation period should depend on your needs. 29072019 AES Encryption Keys password hashing Gerrit Jansen van Vuuren.
 Source: pro-bravia.sony.net
Source: pro-bravia.sony.net
05082018 The key rotation period should depend on your needs. If I print out aesKey I get. That being said the safest. At the end of the day its about key. SecretKey aesKey KeyGeneratorgetInstance AESgenerateKey.
This site is an open community for users to share their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site helpful, please support us by sharing this posts to your favorite social media accounts like Facebook, Instagram and so on or you can also save this blog page with the title how to store aes encryption key by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.






